CM-74 Wireless High Speed Internet
We are the leader in delivering innovative communications, information and entertainment. We offer voice, data and video products and services over intelligent wireless, broadband and global IP networks that meet customers growing demand for speed, mobility, security and control. As a committed corporate citizen, we use our advanced communications services to address important issues confronting our society.Resize Ubuntu VM disk
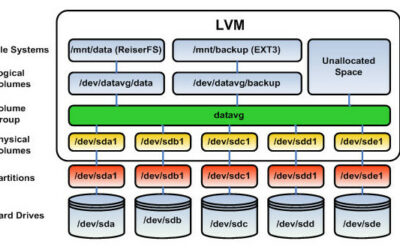
How to resize a logical volume with 4 simple LVM commands 1st step Increase/resize disque from GUI console of your hypervisor 2nd step Extend physical drive partition check free space: sudo fdisk -l Extend physical drive partition: growpart /dev/sda 3 See phisical...
SKY Q – Disable WiFi and use Ethernet only
Before you start make sure your SKY Q box is connected by Ethernet cable. Disabling WiFi on your SKY Q box is done in the SKY Q hidden menu. Press the ‘Home’ button on your remote control. Scroll down to ‘Settings’ and DO NOT press select. Press ‘001’. Press ‘Select’...
How To Configure Unifi UDM-PRO Security Settings
Welcome to this tutorial where I will guide you through the process of configuring Unifi’s Network Security Settings to help you properly secure your networks. With the increasing number of cyber threats, it is essential to have a secure network to protect your data and devices.
In this tutorial, we will be using a Unifi UDM-Pro, a powerful router and security gateway, to configure the network security settings. By the end of this tutorial, you will have a good understanding of how to set up basic security features such as firewall rules, intrusion prevention, and SSL/TLS certificate configuration.
Securing your network is a crucial step towards safeguarding your data and devices from malicious attacks. By taking the time to properly configure your network security settings, you can reduce the risk of unauthorized access and ensure that your network remains protected. So, let’s get started and learn how to properly configure Unifi’s Network Security Settings to secure your networks.
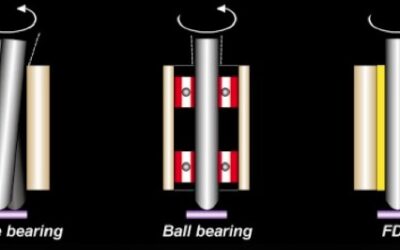
Fan speed, Bearings and Noise
Fluid Dynamic Fans by nature are more robust than traditional Sleeve bearing, or Ball Bearing units. They are fully lubricating, with high anti shock characteristics and have a life span in excess of 100,000 hours. A standard sleeve bearing fan by comparison would be rated between 30,000 and 50,000 hours maximum. The oil way in the center area of the shaft keeps it lubricated. Lower friction also helps reduce noise and temperature, enhancing life span
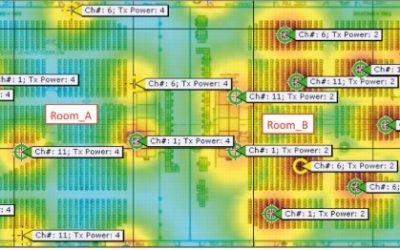
WiFi power level of Cisco access points
Power, power power.... One of the MOST important design factors is selecting the proper radio TX power for WiFi access points when designing any wireless network. You must consider your lowest common denominator and adjust your power equally between your client and AP...
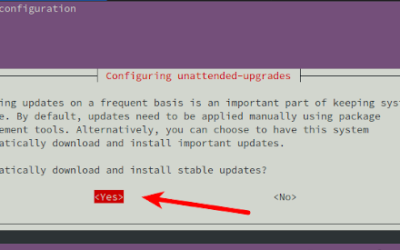
How to set up automatic updates for Ubuntu Linux 18.04
How do I configure automatic updates for Ubuntu Linux 18.04 LTS “Bionic Beaver” server? The Linux server security is indeed an essential task for sysadmins. One of the most fundamental ways to keep the server secure is by installing security updates on time to...
Exploring Crosstalk in Copper Cable Networks
If you're familiar with copper cabling, then you've probably heard about crosstalk - the unwanted phenomenon that occurs when a signal transmitted on one pair or channel causes interference on another. Crosstalk can cause errors and prevent data transmission, making...
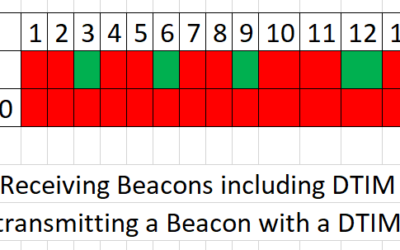
DTIM Interval
Have you noticed that the battery life of your device isn’t what it used to be? Sure, over time your battery will discharge faster and will eventually need to be replaced, but before you pull out your wallet to purchase a pricey new battery for your laptop or...
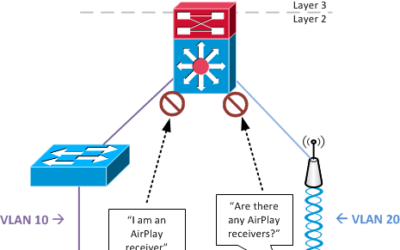
Secure Home Network – Using AirPlay Across VLANs
In a previous post, I discussed why you should isolate connected devices with VLAN. Smart TVs ideally should be in the Device VLAN, too, instead of your “secure” VLAN. But putting them on a separate VLAN breaks an important TV use case for cord cutters: AirPlay....
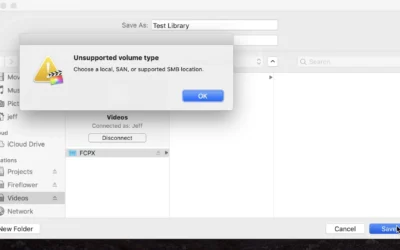
Final Cut Friday: How to store FCP X libraries on a Synology NAS
If you try to save or open a Final Cut Pro X library on an Synology NAS that hasn’t been configured properly, you’ll receive the following frustrating error message: Unsupported volume type – Choose a local, SAN, or supported SMB location.The good news is that with...
How to install an SSL Certificate on Aruba ClearPass?
In this article, you will learn how to generate a CSR code and install an SSL Certificate on Aruba ClearPass Policy Manager (CPPM). Besides configuration instructions, you will also discover a few interesting facts about Aruba ClearPass. Finally, in the last section,...
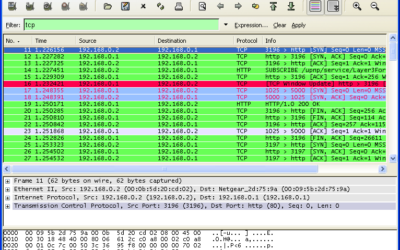
Wireless Wireshark Filters
Basic filter: wlan.addr == 00:11:22:33:44:55 (Mac address) Filter on only authentication: wlan.addr == 00:11:22:33:44:55 (Mac address) && wlan.fc.type_subtype == 0x000b Filter on only association request: wlan.addr == 00:11:22:33:44:55 (Mac address) &&...
Confused by protocols? Keep it simple
When is a standard not a standard? For me the answer is clear. It’s when you are effectively at the mercy of a manufacturer to keep supplying and supporting the devices you specify as part of what is probably a five-figure project. If they don’t (and we’ve probably...
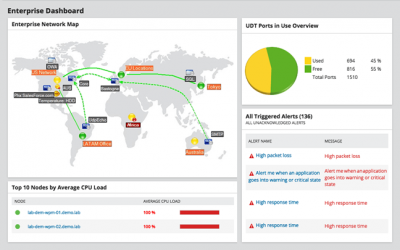
Network monitoring and management
Most IT buyers put network monitoring and management tools in place and expect them to just work. Unfortunately, the tools require upfront planning, detailed configuration and ongoing maintenance to ensure the technology delivers on its promise. Inventory...
9 reasons to turn down the transmit power of your Wi-Fi
By default almost all WiFi access points transmit at full power (100mW on 2.4GHz). This gives maximum coverage and users see a good signal (“full bars”). However, there are good reasons to turn down the transmit power to a fraction of the maximum. It even makes sense...
XenServer – Secure SNMP Installation (Version 3)
This tutorial describes a detailed procedure showing how to perform the installation of Secure SNMP (Version 3 ) on a computer running XenServer Remotely access the XenServer server via SSH. In our example, we are using the putty software to remotely...
UniFi – Where is ?
You will see in many of our configuration instructions. When following these instructions you are supposed to substitute with the corresponding location in your computer. Its location will vary depending on your operating system. Find in the following...
How to sync your Microsoft OneDrive cloud storage with Linux
While Microsoft has been making a lot of progress in supporting open source software, and released things such as SQL Server on Linux, their support for consumer software is still lacking. But while applications like Office are still not available for...
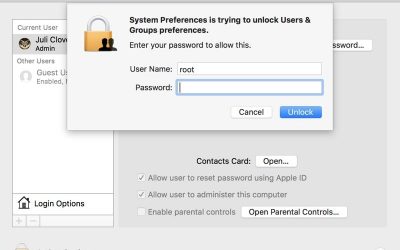
Major macOS High Sierra Bug Allows Full Admin Access Without Password – How to Fix
There appears to be a serious bug in macOS High Sierra that enables the root superuser on a Mac with a blank password and no security check. The bug, discovered by developer Lemi Ergin, lets anyone log into an admin account using the username "root" with...
PC vendors scramble as Intel announces vulnerability in firmware
Millions of computers could be remotely hijacked through bug in firmware code. Intel has issued a security alert that management firmware on a number of recent PC, server, and Internet-of-Things processor platforms are vulnerable to remote attack. Using...
Wi-Fi KRACK, How to Protect Yourself
It was this morning revealed every Wi-Fi network is potentially at risk as a result of a vulnerability called 'Wi-Fi KRACK'. It allows 'snoopers' to eavesdrop on traffic between network devices (i.e. computers, laptops and tablets) and a wireless access...