A month after the WannaCry ransomware attack paralyzed connected systems worldwide, a new threat appears to be spreading quickly.
As reports emerge, today’s attack paints a picture of businesses and governments around the world held hostage by a second major wave of ransomware, a kind of software that hijacks computerized systems and demands payment, often in bitcoin, to unlock them.
Initially it appeared that the ransomware might center on Ukraine, though reports since then have confirmed that it also is affecting systems in Spain, France, Russia and India. Anecdotally, many more countries may be affected as governments and businesses around the world find themselves locked out of their own machines.
According to a researcher at Kaspersky Lab, the ransomware appears to employ a forged Microsoft digital signature that exploits a Microsoft Office vulnerability that security firm FireEye discovered in April. So far, the ransomware appears to have targeted a number of global banks, including Russia’s Rosneft and Ukraine’s state-owned Oschadbank.
Update: Some reports suggest that confusion about a simultaneous incident in Ukraine means that the global attack may not actually be using Microsoft’s CVE-2017-0199 vulnerability.
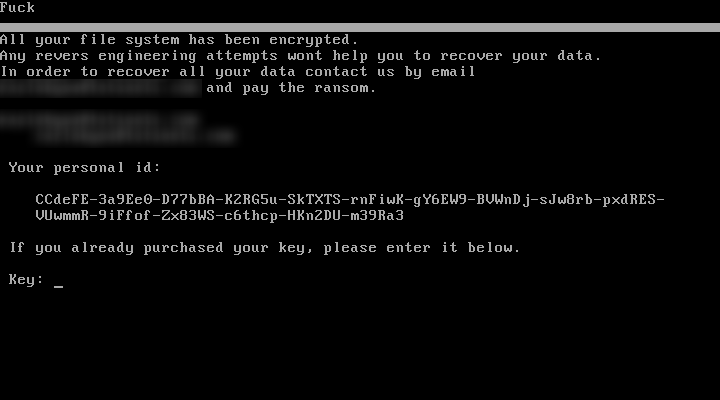
Early reports suggest that like WannaCry, Petya is using the leaked NSA exploit known as EternalBlue to spread. The ransomware known as Petya (also called Petrwrap) is well known to security researchers and may have been commercially available on dark web software exchanges for some time.
Everything about this situation indicates that plenty of governments and companies around the world didn’t take WannaCry seriously, failed to patch their systems and are now paying the price.