Key Knowledge
- An Intrusion Prevention System (IPS) is a type of engine that identifies malicious traffic by checking the signatures. The signatures contain known traffic patterns or instruction sequences used by malware. This type of signature-based engine can only detect anomalies based on known malicious traffic patterns.
- An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or computer. IDS only listens for issues and alerts you and does not take preventative action.
- GeoIP Filtering is a technology that can block web traffic from entire countries, can be an effective way to stop hackers from attacking your business. As the name suggests, it blocks network connections based on geographic location – information it gets based on IP addresses. This can then be used to filter and prevent both outgoing and incoming connections to and from your network.
- Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep packet inspection is often used to baseline application behavior, analyze network usage, troubleshoot network performance, ensure that data is in the correct format, check for malicious code, eavesdropping, and internet censorship, among other purposes.
- Unifi Endpoint Scanner, this application will scan your network and document your devices Operating System version, IP addresses and opened ports. This provides you with a visibility into system ports that should not be opened throughout your environment .
- Unifi UDM-PRO also has a deployable Honeypot. This honeypot system intended to mimic likely targets of cyberattacks. It can be used to detect attacks or deflect them from a legitimate target. It can also be used to gain information about how cybercriminals operating within your network.
- DNS Filtering is a engine that will block malicious websites and keep company data secure. DNS filters ensure that employees don’t access inappropriate content or get viruses from visiting malicious sites. This is often part of a larger access control strategy.
- Device Isolation is an option that is best used in networks for Guests and IOT devices, this blocks communication between clients on the same local network.
Lets Get Started
We will be configuring everything within the Unifi UDM-Pro that you have learned from the Key Knowledge above.
- Make sure your Unifi Firewall and Unifi Controller is fully updated.
Configuring IDS/IPS
In this section we will be ignoring IDS and will be utilizing the full feature IPS engine.
- Log into your Unifi Controller.
- Click on Settings > Traffic & Security > Global Threat Management.
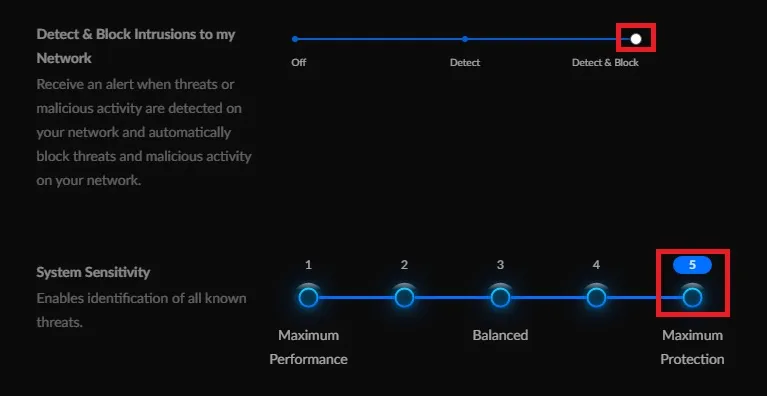
- Under Detect & Block Intrusions to my Network move the slider all the way to the right for Detect & Block.
- Under System Sensitivity Select Maximum Protection.
Configuring GeoIP Filtering
In this section we will be configuring Country Access Restrictions.
- Log into your Unifi Controller.
- Click on Settings > Traffic & Security > Global Threat Management.
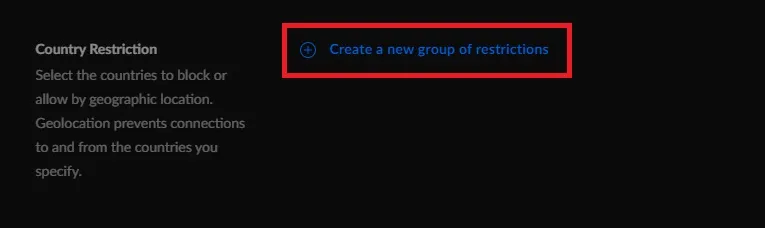
- Locate Country Restriction and click on Create a new group of restrictions.
- Your restriction should Block both traffic directions. For example I am blocking China, Russia and North Korea.
- Once your Country selections are made, Click the button Add Restriction.
Configuring DPI and Endpoint Scanner
In this section we will be configuring Deep Packet Inspection and Endpoint Scanner.
- Log into your Unifi Controller.
- Click on Settings > Traffic & Security > Traffic & Device Identification.
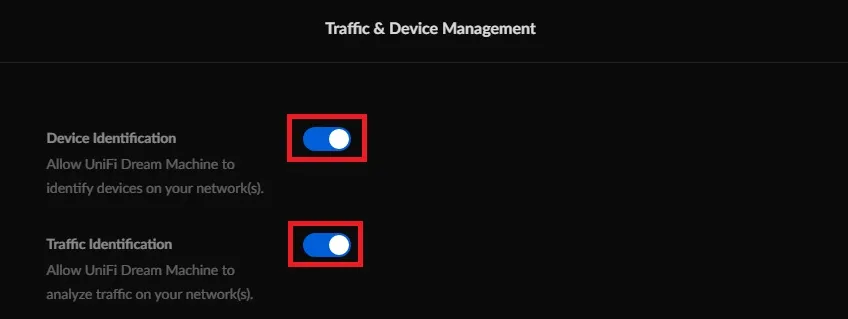
- Enable Device Identification.
- Enable Traffic Identification.
Configuring a Honeypot
In this section we will be configuring Deep Packet Inspection and Endpoint Scanner.
- Log into your Unifi Controller.
- Click on Settings > Traffic & Security > Global Threat Management.
- Scroll down and click on Advanced Features and Customization to expand. We will be enabling some advanced protection features.
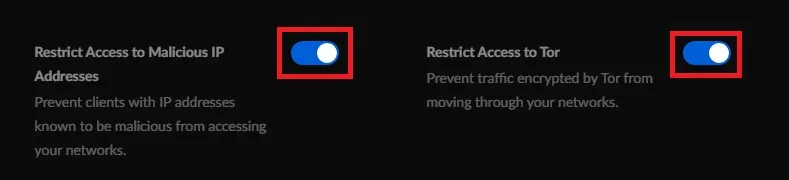
- Enable Restrict Access to Malicious IP Addresses.
- Enable Restrict Access to Tor.
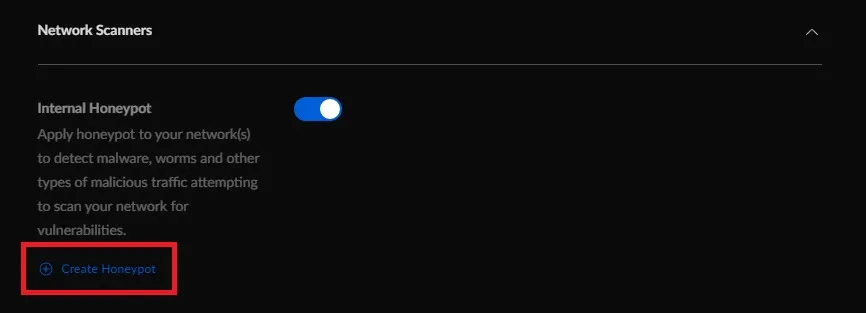
- Locate and expand Network Scanners.
- Click on Create Honeypot.
- Select your Network.
- Assign an IP Address outside DHCP to this honeypot that matches your selected networks subnet LAN.
- You can also configure a Honeypot for every VLAN.
Configuring DNS Filtering
In this section we will be configuring DNS Filtering or also known as Content Filtering.
- Log into your Unifi Controller.
- Click on Settings > Networks > Click on any of your Networks.
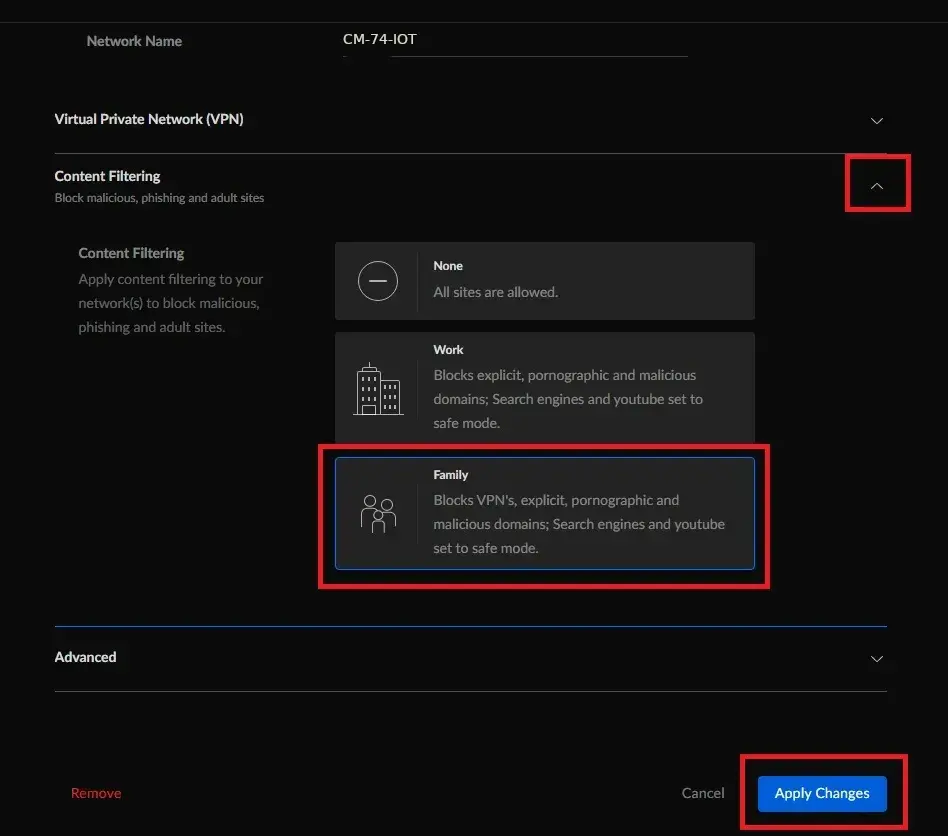
- Locate and click on Content Filtering to expand.
- Select your use case, Work or Family.
- Click the button Apply Changes.
Configuring Device Isolation
In this section we will be configuring DNS Filtering or also known as Content Filtering.
- Log into your Unifi Controller.
- Click on Settings > Networks > Click on your Guest or IOT network vLAN.
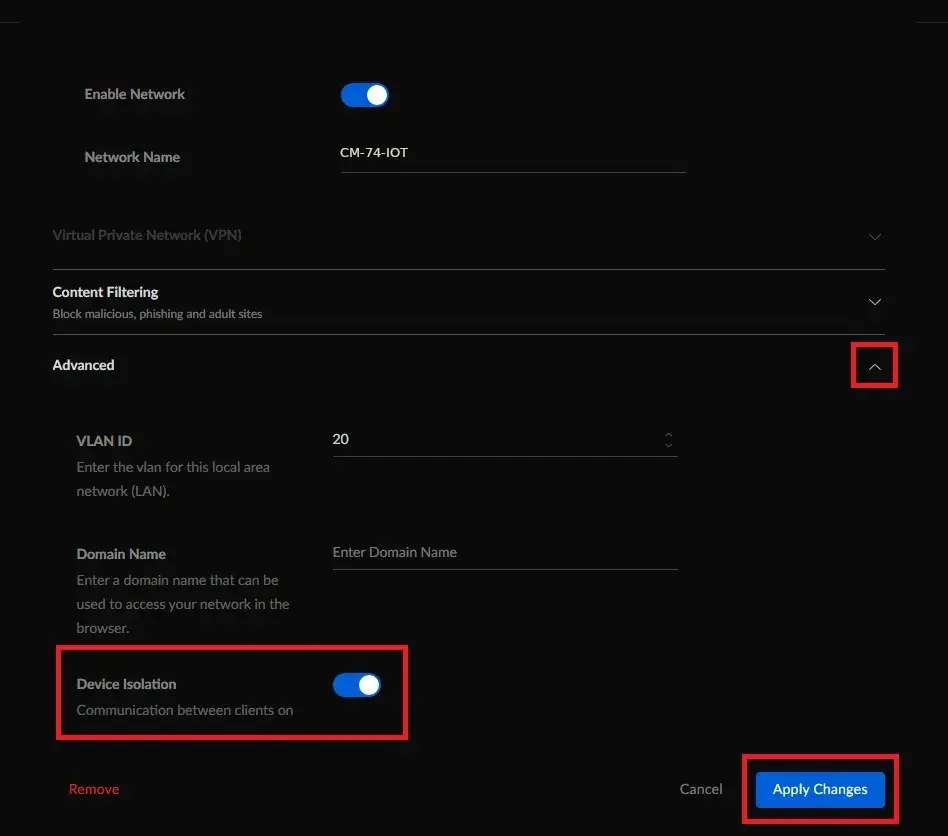
- Locate and click on Advanced to expand.
- Locate Device Isolation and enable it.
- Click on the Apply Changes button.