CM-74 Wireless High Speed Internet
We are the leader in delivering innovative communications, information and entertainment. We offer voice, data and video products and services over intelligent wireless, broadband and global IP networks that meet customers growing demand for speed, mobility, security and control. As a committed corporate citizen, we use our advanced communications services to address important issues confronting our society.Block Websites Using DPI
Here is an example of configuring a custom application category and firewall rule to block traffic for Facebook. You could also use the default application categories or create other custom categories. configure #If DPI is not already enabled set system...
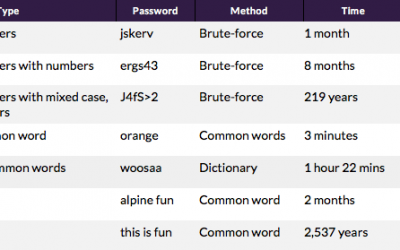
Setting a Secure Password
When choosing your password we recommend using 3 word password phrases to set your passwords, rather than complex gibberish types. There are several freely available password cracking tools out there and there are 3 common techniques to crack a password: Brute force =...
EdgeMAX – Web proxy service for filtering
How the web proxy service can be configured via EdgeRouter's CLI? A web proxy is useful for blocking, allowing or redirecting web traffic. There are a number of options associated with the web proxy service: hg@optusnet# set service webproxy ? administrator...
The 5 Key Aspects of a Top Trading Computer
Our expertise in multi-screen computer systems means that we serve customers in a few different markets however our largest sector has to be the trading / financial area. We have supplied specialist trading computers for over 4 years now and have spoken with hundreds...
How to enable SNMPv3 on Linux (Ubuntu or Debian)
The information on getting SNMPv3 up and running on Linux is somewhat fragmented on the...
How to install the UniFi Controller on Ubuntu
Ubiquiti UniFi is properly supported on Ubuntu and Debian, breaking away from being Windows only. Being on Linux also reduces a lot of overhead that Windows typically laid on. The...
Flex or cable? There are two types of electric wiring: flexible cords (flexes) (1) connect electrical appliances to the mains via plugs; cables (2) are used for permanent wiring around the house. There are many sizes and types of flexible...
What You Need to Know About Multi Monitor Graphics Cards
The Short Version The best way to achieve a stable and silent multi-screen computer which can survive a dying graphics card is to use multiple, passively cooled, dual monitor graphics cards. Most non-gaming quad monitor graphics cards perform poorly and are expensive,...
MySQL Database User: Which Privileges are needed?
For normal WordPress operations, such as posting blog posts, uploading media files, posting comments, creating new WordPress users and installing WordPress plugins, the MySQL database user only needs data read and data write privileges to the MySQL database; SELECT,...
Securing WordPress
Security in WordPress is taken very seriously, but as with any other system there are potential security issues that may arise if some basic security precautions aren't taken. This article will go through some common forms of vulnerabilities, and the things you can do...
EdgeMAX dhcp-server configuration
After setup DHCP servers in the network you may discover problem with a slow response from DHCP server. This is very common problem when the network use a segmentation. Usually each of VLAN required own DHCP server. To correct this problem you should...
How to install the UniFi Controller on CentOS
How to install UniFi controller on CentOS, a very stable Linux platform used on production servers. Prepare CentOS # yum update -y # reboot # yum -y install wget unzip php httpd # service httpd start # chkconfig httpd on # su root MongoDB # vi...
How to connect terminal to Serial-USB device on Ubuntu
List your all USB peripheries lsusb Connect your USB serial cable and list all USB peripheries once again. Note the new device (like 0557 an 2008) mobprobe usbserial vendor=0x0557 product=0x2008 dmesg | grep 'ttyUSB' note: ttyUSB0 chmod 777 /dev/ttyUSB0 To connect...
Unix/Linux command reference
File Commands ls – directory listing ls -al – formatted listing with hidden files cd dir - change directory to dir cd – change to home pwd – show current directory mkdir dir – create a directory dir rm file – delete file rm -r dir – delete directory dir rm -f file –...
Ten Ways to Protect Your IT Infrastructure
Reduce Costs while protecting critical business systems. If you have wondered how to provide serious protections on a small-business budget, this article is for you. Learn about power, cooling and security issues that put your IT systems at risk. Find out how to...
How to add a Swap File in Linux
In Linux, as in most other Unix-like operating systems, it is common to use a whole partition of a hard disk for swapping. However, with the 2.6 Linux kernel, swap files are just as fast as swap partitions, although I recommend using a swap partition. The...
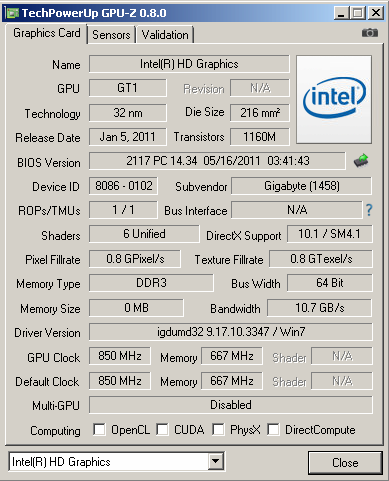
Integrated Intel GPUs that you can Mine Crypto Coins On with OpenCL
GPU-Z is a lightweight utility designed to give you all information about your video card and GPU. If you are really willing to squeeze every little bit of performance for mining crypto coins with your available hardware you should be aware of the fact that you can...
Windows Update download tools
In this article, we examine four Windows Update download tools that allow you to download all updates for the various Windows versions. This enables you to perform offline updates or slipstream the updates into a Windows image. Updating Windows through Microsoft...
Easily add drivers and updates to images with GUI 4.0 DISM
One of the greatest advantages to using Microsoft for Imaging is the ability to perform offline image patching and keep images up to date rather than rebuilding your base image every time a major update or service pack is released. Deployment Image Servicing and...
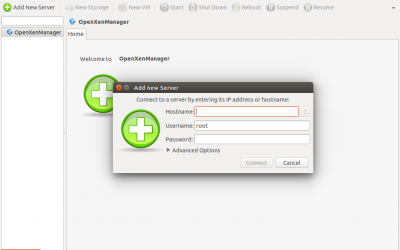
How to install XenCenter on Linux
Citrix XenCenter is client software with GUI for managing XenServer/XCP hosts remotely. Using XenCenter, you can create virtual machines (VMs), access VM consoles, and configure VM storage and networking. As of this writing, Citrix only offers a Windows native client...
Creating a .pem File for SSL Certificate Installations
.pem SSL Creation Instructions SSL .pem files (concatenated certificate container files), are frequently required for certificate installations when multiple certificates are being imported as one file. This article contains multiple sets of instructions that walk...